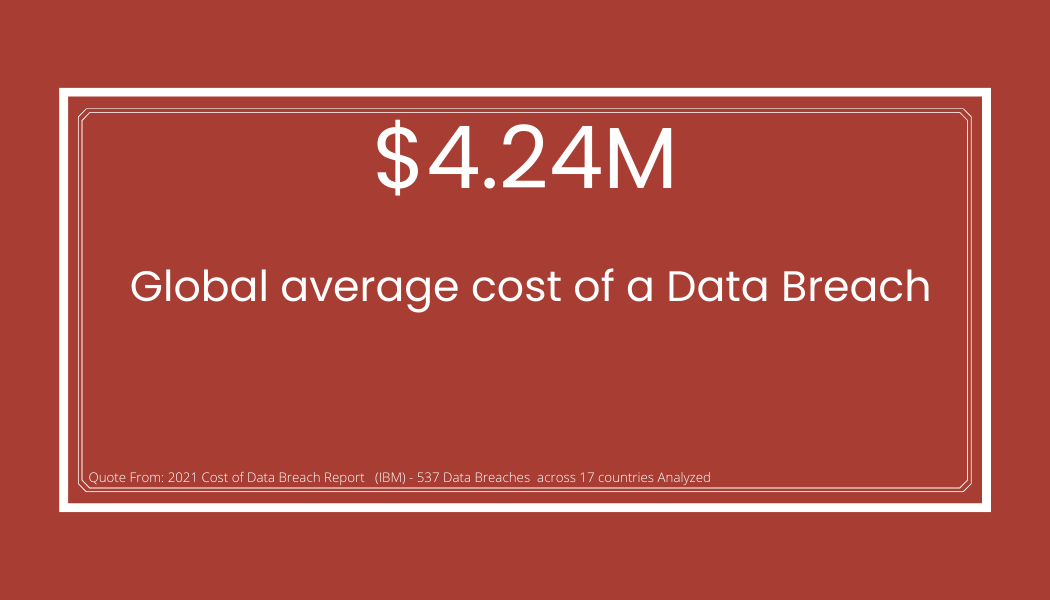
On average, lost business due to a data breach is $1.59M, based on a global average $4.24M cost. Clients and partners need to be confident in your abilities to prevent a data breach
JAAG and its service partner, Fortis, have looked at some basic certifications that are simple, timely, and cost effective, to accomplish and provide confidence that you are able to handle Cybercrime effectively.
Cyber Essentials, Cyber Essentials Plus, and IASME Governance certification, can provide confidence that you are taking care of Cybercrime in your business.
Designed specifically for SMEs, these certificates are a mark of confidence, established in Europe and the UK by appropriate governments for SMEs to conduct their business and be considered Cybersafe!